Next: Annexe : CV
Up: Projet ASPIC:Algorithmes et Systèmes
Previous: Diffusion de l'Information
- 1
- Bermond,et al Diffusion dans l'hypercube, Annales de
l' Institut Fourier,
- 2
- S. Boztas
Near-optimal 4-phase sequences and optimal binary sequences
for CDMA,
University of southern California, 1990.
- 3
- J.H. Conway and N.J.A. Sloane,
Sphere Packings, Lattices and Groups,
Springer-Verlag, 1988
- 4
- O. Goldreich, S. Goldwasser, S. Halevi,
Public-key Cryptostems from Lattice Reduction problems,
Springer Lect. Not. in Comp. Sc. 1294 (1997) 112-131.
- 5
- A. R. Hammons, Jr., P. V. Kumar
On a Recent Four-Phase Sequence Design,
Special Issue on Spread-Spectrum Techniques and Applications
of the IEICE Trans. on Communications, vol. E 76-B, No. 8, pp. 804-813, August 1993.
- 6
- S. Boztas, R. Hammons, and
P.V. Kumar,
4-Phase Sequences with Near-Optimum Correlation
Properties,
IEEE Trans. on Inform. Theory, vol. IT-38, 3, pp. 1101-1113, May 1992.
- 7
-
S. Loureiro.
Mobile Code Protection
Thèse de l'ENST, EURECOM, Jan. 2001.
- 8
- http://www.ntru.com/technology/index.htm
- 9
- P. Solé,
A Quaternary Cyclic Code, and a Familly of Quadriphase
Sequences with low Correlation Properties,
Lect. Notes Computer Science, 388,1989, pp. 193-201.
- 10
- P. Solé, C. Charnes,
B. Martin,
A lattice-based McEliece scheme for encryption and
signature,
WCC 2001, Jan. 2001, Paris.
- 11
- A. Bonnecaze, P. Solé, C. Bachoc, B. Mourrain, ``Type II Codes over
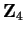 '' ,
IEEE Trans. on Information
Theory, IT-43 (1997) 969-976.
'' ,
IEEE Trans. on Information
Theory, IT-43 (1997) 969-976.
- 12
- A. Bonnecaze, B. Mourrain, P. Solé ``Type II codes, Jacobi polynomials,''
and designs, Designs, Codes and Cryptography vol 16, (1999) 215-234.
- 13
- Y-J. Choie, B. Mourrain, P. Solé,``Rankin-Cohen brackets and
Invariant Theory'' J. of Algebraic Combinatorics.
- 14
- C. Charnes, B. Martin, P. Solé, A lattice based McEliece
scheme for encryption and signature, Actes de WCC01,
Paris 2001, 497-506.
- 15
- Chen X., Reed I. S., Helleseth T., Truong T.K.,
``Use of Gröbner bases to decode cyclic codes up to the true minimum
distance'', IEEE Trans. on Information Theory 40 (1994) 1654-1661.
- 16
- N. Koblitz, Algebraic Aspects of Cryptography, Springer,
Algo and Comp. in Mathematics, Vol. 3
(1998).
- 17
- J. Galtier, P. Solé, A. Vardy, On the covering
radius of lattices, en préparation.
- 18
- R. Hammons, V. Kumar, A.R. Calderbank,N.J.A. Sloane, P.
Solé,``Kerdock, Preparata, Goethals and others are linear over
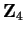 .''
IEEE Trans. of Information Theory vol. IT-40 (1994) 301-319.
.''
IEEE Trans. of Information Theory vol. IT-40 (1994) 301-319.
- 19
- Keith Saints, Chris Heegard,
Algebraic-Geometric Codes and Multidimensional cyclic codes: a unified
theory and algorithms for decoding using Gröbner bases, IEEE Trans. on
Information Theory 41 (1995) 1733-1751.
- 20
- A. Kelarev, P. Solé
``Error-correcting codes as ideals in group rings'',
Proceedings of AGRAM 2000, Perth, 2000.
- 21
- M.E. Hellman, R.C. Merkle, Hiding Information and Signatures
in Trapdoor Knapsacks, IEEE Trans on Information Theory 24 (1978) 525-530.
- 22
- G. Norton, A. Salagean, Strong Gröbner bases and cyclic
codes over finite chain rings, Actes de WCC01, Paris 2001, 391-402.
- 23
- www.ntru.com
- 24
- Jeffrey Hoffstein, Jill Pipher, Joseph H. Silverman,
NTRU: A Ring Based Public Key Cryptosystem, Springer Lect. Not. in Comp. Sc. 1423 (98) 267-288.
- 25
- Jeffrey Hoffstein, Daniel Lieman, Joseph H. Silverman,
Polynomial Rings and Efficient Public Key Authentication,
in Proceeding of the International Workshop on Cryptographic Techniques and
E-Commerce (CrypTEC '99), M. Blum and C.H. Lee, eds., City University of
Hong Kong Press, to appear.
- 26
- A. Shamir, A polynomial time algorithm for breaking the basic
Merkle-Hellman cryptosystem IEEE Trans. Information Theory 30 (1984)
699-704.
- 27
- Tribune de l'économie, 22 Novembre 2000
La chasse aux cryptographes français est ouverte. p. 22-23.
Alexis Bonnecaze
2001-03-05